
How to Identify & Prevent Phishing Attacks
Phishing is a technique used by attackers to trick individuals into divulging personal information — like login credentials — or launching malware to steal broader sets of data stored on their computers or connected networks.

One of the largest risks for any company is phishing. It is one of the top ways to compromise a company. Phishing is so prevalent, it’s hard to find someone who hasn’t experienced it by now. And as bad actors become more savvy, it’s important for professionals to equip themselves with the right tools to safeguard their most sensitive data.
Phishing is a technique used by attackers to trick individuals into divulging personal information — like login credentials — or launching malware to steal broader sets of data stored on their computers or connected networks. A phish typically looks like a valid email from a trusted source, duping recipients into opening the email and clicking on enclosed attachments or links.
The Anti-Phishing Working Group observed more than five million phishing attacks in 2023. According to the 2024 Verizon Data Breach Investigation Report, 68 percent of data breaches were caused by human mistakes. These figures highlight the importance of ensuring employees are properly trained to identify, flag and report suspicious emails.
In this post, we highlight key tips to protect your organization from phishing attacks.
Learn how to stop and recognize phishing
One of our top priorities is to make your Docusign experience as safe and secure as possible — trust is in our DNA and ingrained in our people, processes, and platform (Docusign Trust and Security Overview).
We are committed to employing the latest technology and industry knowledge to keep our customers safe from attackers, but it takes awareness and commitment from everyone involved to achieve the highest level of security. Learning how to recognize suspicious emails is the best way to protect yourself and your data.
Ask yourself the right questions
Generally, it’s best to be skeptical about strange emails. Here’s a quick checklist of questions you can run through to ensure an email is legitimate:
Are you expecting the email?
Do you recognize the sender?
Do the email signature and the sender name/email address match?
If it's a Docusign email, does it have the new and correct logo and branding?
Is the look or tone off from the norm?
Are there spelling or grammar errors throughout?
Is it more generic than it should be?
Is it asking for you to provide your personal or login information?
Are the links taking you to a valid and expected place (hover over them without clicking on your computer or long tap on your mobile device to see the link)?
Are there strong emotions or an urgency communicated?
Do you feel like it’s just weird?
Some additional layers of protection against phishing are to:
Enable multi-factor authentication, when possible
Use strong and unique passphrases
Ensure your antivirus software is up to date
How to detect Docusign-themed phishing attempts
A few simple techniques can help you spot the difference between a spoofed Docusign email and the real thing:
Don’t open unknown or suspicious attachments or click links — Docusign will never ask you to open an office document or zip file in an email
Hover over all embedded link URLs — to view or sign Docusign documents only containing “docusign.net/” and ensure they always start with “http”
If the the email contains a QR code, verify the source by checking associated links, email addresses, and phone numbers before scanning
Access your documents directly from www.docusign.com by entering the unique security code, which is included at the bottom of every Docusign email
Report suspicious Docusign-themed emails to your internal IT/security team and to verify@docusign.com
Ensure it has the correct Docusign logo and branding
A Docusign site link will begin with “https://www.docusign.net”; the link may also include a subdomain from one of our other servers like, “na2”, “na3”, “na4”, “au”, “ca”, “eu” or “demo” designations.
Note: in the final email you receive that states the envelope is complete, you may receive a completed PDF signed document as an attachment.
Fake Docusign examples
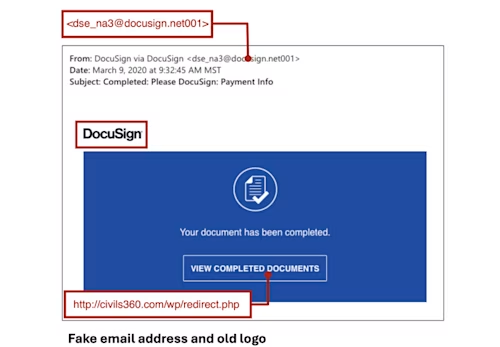
In the first two examples below, the URLs don’t start with “https” nor do they include “docusign.net”. They both use old Docusign logos.

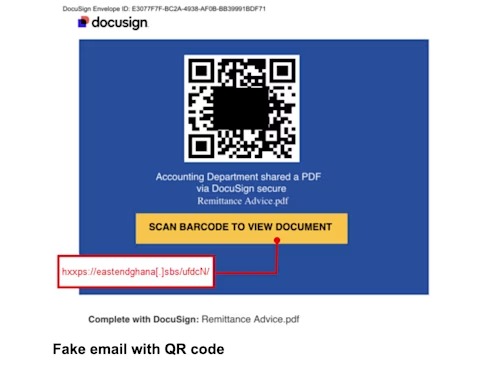
In this third example, it shows “quishing” where an attacker attaches a malicious QR code to a fake Docusign envelope. When scanned, the QR codes send recipients to fraudulent websites that attempt to capture login credentials.
Before scanning a QR code, double-check other information provided in the message; hover over and verify links, check email addresses and phone numbers
Don’t use personal devices to scan QR codes from work emails
How Docusign protects against phishing
Docusign proactively detects and deters phishing attempts by tapping into the deep expertise and experience of the Docusign security team in combination with sophisticated automated techniques, including:
Leveraging custom automation tooling (developed in conjunction with the Docusign security team) to process potentially fraudulent URLs submitted to verify@docusign.com by customers or reported in threat intelligence feeds
Utilizing machine learning algorithms to improve accuracy and reduce false positives when identifying phishing attempts
Using performance dashboards and visualizations to track phishing trends over time and analyze phishing pages in real time
Enforcing a DMARC (Domain-based Message Authentication, Reporting and Conformance) reject policy on Docusign.net, so any spoof email purportedly sent from docusign.net is rejected by all email providers supporting DMARC, after which the email content is sent to Docusign for analysis
Partnering with leading security vendors and law enforcement organizations to share, take down and add to deny lists any malicious websites and prevent further phishing attacks
For Docusign security and system performance information, visit the Docusign Trust Center.
Related posts
Docusign IAM is the agreement platform your business needs


