Detect, Investigate and Respond to Potential Threats with Docusign Monitor
Docusign Monitor helps protect your agreements with round-the-clock activity tracking. Customize alerts to quickly respond to unauthorized activity.


Preventing damage from unauthorized activity is a critical challenge for organizations. A 2020 study by the Ponemon Institute revealed that 7% of malicious breaches were caused by unauthorized insider activity, and an additional 19% by stolen or compromised credentials. And the activity doesn’t need to be malicious to cause harm: the same study attributed 23% of all breaches to human error, including negligent actions by employees and contractors.
The importance of managing risk from unauthorized activity resonates with major organizations as they transform their agreement processes. After all, while Docusign meets or exceeds stringent Canada, US, EU, and global security standards, an organization’s system of agreement can only be as secure as their own credential management and operational integrity. That’s why it’s no surprise that some of Docusign’s premier customers have asked for greater visibility into these factors, to help them address threats that can arise from unauthorized activity.
Introducing Docusign Monitor
Docusign Monitor helps protect your agreements with round-the-clock activity tracking. It provides near real-time visibility into your operations as they relate to your Docusign agreements and processes. Using advanced analytics to track Docusign web, mobile, and API account activity across your organization, Monitor helps security teams:
Detect potential threats
Investigate incidents
Respond decisively
Detect potential threats with rules-based alerts
Monitor surfaces many types of events related to your account activity—like login attempts, password changes and envelope deletions—to help identify internal or external threats. It comes with pre-built alerts for common types of suspicious activity, such as when a user deletes too many envelopes in a short period of time, or a delegated admin removes a signer authentication requirement.
Investigate incidents with actionable information
Monitor provides ready access to detailed information about the activities that triggered the alert, including IP address, location and device type. Armed with this actionable information, security teams can efficiently prioritize and investigate incidents to determine if a genuine threat exists.
Respond to threats with decisive action
Monitor enables teams to address verified threats quickly with appropriate action, such as closing a compromised account before it can cause significant harm. Remediating threats early is a great way to contain damage related to unauthorized activity, which is why security teams continue to adopt activity insight and security automation tools.
Connect Monitor to your existing security stack
Monitor also includes an API that can deliver this activity information directly to your existing security stack, integrating easily with the software you’re already using—including Security Information and Event Management (SIEM) tools like Splunk or Sumo Logic, and data visualization tools like Tableau or Power BI. This gives your team flexibility to tailor dashboards and alerts to meet your particular industry, security, and regulatory requirements.
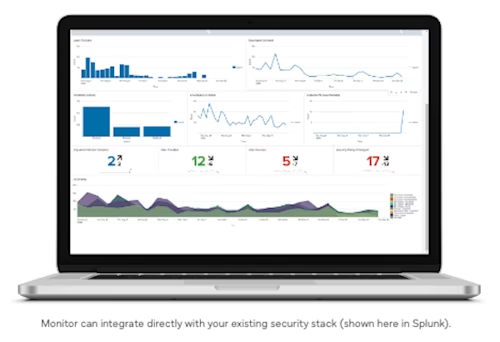
As your Docusign use-cases continue to grow, Monitor can be a powerful tool to bolster the integrity of your systems, reinforce company policy and help assure your customers that their sensitive data is in good hands.
Safeguard your agreements with Docusign Monitor.
Contact us for a demo.
Related posts
Docusign IAM is the agreement platform your business needs