Enriching your IOC stack through third-party security analytics

By Roland Dela Paz, Senior Information Security Engineer, Docusign
Using security analytics from third-party tools to enrich your threat intelligence could provide fresh indicators of compromise (IOCs) or save you the cost of commercial intelligence feeds.
Sources for IOCs
IOCs are an integral part of a security operations center’s (SOC) day-to-day operations. They provide us visibility to known threats that may be present in our network. Traditionally, we collect these precious IOCs through honeypots, open source intelligence (OSINT), or even paid commercial feeds. A less obvious source of IOCs, however, are third-party security analytics that you may already be using in your environment.
Email security appliances as a source for IOCs
In a traditional sense, we rely on email security appliances largely to either create policies or block bad emails through the appliance’s analytics. However, if logging is enabled, metadata of blocked emails are usually available from the logs. We can then “clone” some of the metadata as IOCs, such as embedded URLs, attachments, or even senders, for future alerting.
We can also use the email metadata to check for malicious email campaigns—by monitoring volume per metadata—that may be targeting your organization. For example, a known malicious attachment hash that’s being sent to more than 50 of your employees may indicate a targeted campaign.
Security analytics offered by identity and access management (IAM) vendors
IAM tools are another good example of a third-party solution that you can utilize for new IOCs. The security features can be costly, but these proprietary security technologies not only provide good detections, they also come with descriptive logs for anomalies they detect. With context on the detected IOCs, you can decide how you want to further utilize the IOCs.
These tools may have algorithms to detect password spraying attacks where the offending IPs are logged and tagged as such. They may also have their own set of blacklisted IPs that may not necessarily be available directly to you. However, if one of these IPs appears on your network, it will be flagged and will consequently appear on your logs.
Having a centralized security orchestration automation and response (SOAR) system helps immensely, allowing you to easily propagate collected IOCs to other logs you want them to be checked against.
We also built our own threat intelligence platform (TIP) that allows us to store all IOCs known to us in one place along with their respective contextual data.
This not only allows us to manage IOCs properly, but it also allows us to enrich incident tickets. By querying our TIP, we can easily retrieve, for instance, an IOC’s age, type, source, malicious score, and description.
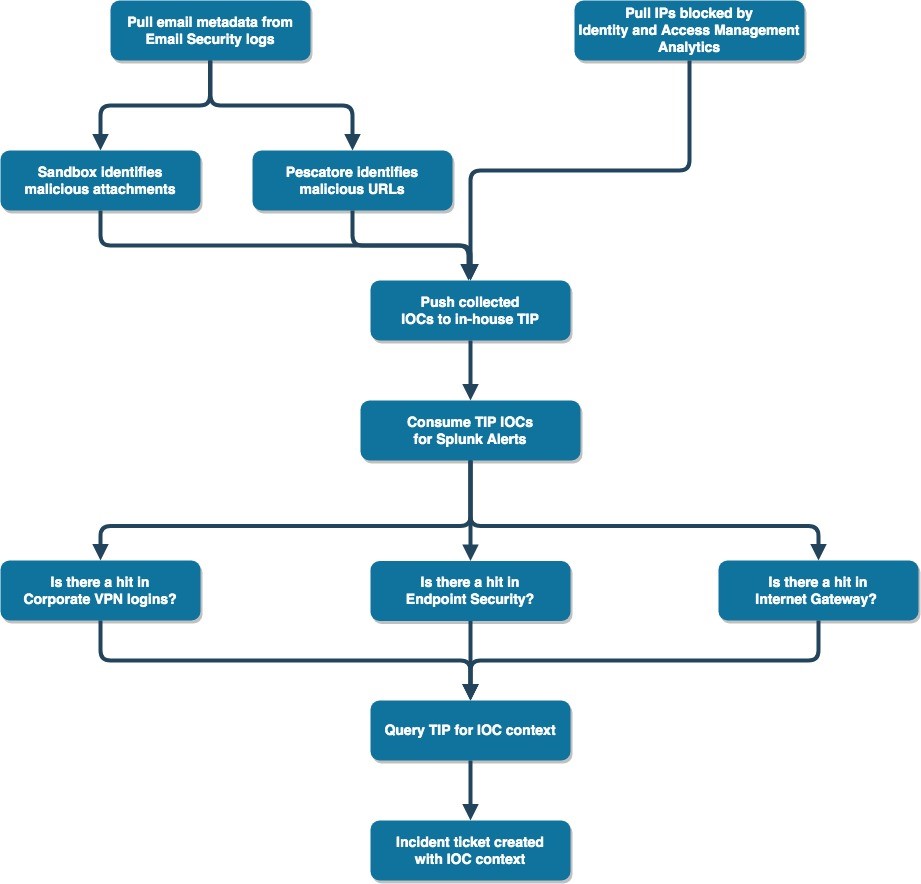
The following chart is a simplified example of this concept. It shows how our in-house tool, Pescatore, contributes to vetting IOCs before we push them to our TIP.
Conclusion
Third-party security analytics are often only viewed as an aid to block anomalies. With proper logging, however, they can be a good source of threat intelligence, often providing fresh IOCs.
This can reduce costs for small to medium sized SOCs if budget is an issue. The budget saved can be used to pay for additional security technologies instead of paying for commercial intelligence feeds outright.
Learn more
To learn more about how Docusign strives to achieve an automation-centric environment, see our blog on the SOAR system that we built in-house
To learn more about Docusign’s in-house tool for vetting IOCs, read Pescatore: A Real Time URL Classification System for SOCs
Related posts
Discover what's new with Docusign IAM or start with eSignature for free



